Cybersecurity Concentration
The Cybersecurity Concentration is for computer science students who want to help protect the security of the future.
As our daily lives increasingly depend on technology, the security and privacy of that technology becomes ever more important. Gain a critical understanding of the technological needs, threats, and weaknesses in cybersecurity with the Cybersecurity Concentration.
Program Highlights

15 CREDIT HOUR CURRICULUM

CUTTING EDGE CURRICULUM WITH PRACTICAL APPLICATIONS

DOES NOT ADD TIME TO DEGREE
Cybersecurity touches multiple disciplines, careers, and nearly all aspects of society—from public policy to energy management to product design. In a time when connected devices could outnumber humans, there is an urgent need for cybersecurity professionals who can solve a multitude of challenges.
8TH
SYSTEMS
U.S. News & World Report, 2018
7TH
THEORY
U.S. News & World Report, 2018
8TH
AUSTIN - CITIES WITH BEST PAYING CYBERSECURITY JOBS
Indeed, 2018
Projected Market Growth

Projected cybersecurity market size from 2017 to 2022 (11.0% CAGR)
Cybersecurity in Demand
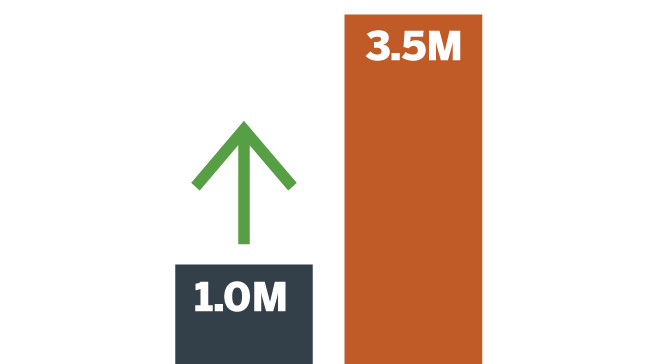
Forecasted unfilled jobs from 2016 to 2021
Cybersecurity Occupations

Cybersecurity unemployment rate through 2021
Cybersecurity concentration students will receive instruction on a wide range of cybersecurity related topics like network security and cryptography. Students will also have the opportunity explore the social ramifications of cybersecurity through courses such as Ethical Hacking.
FOUNDATION COURSES
To earn the Cybersecurity Concentration students will need to complete the following courses:
- CS 346 Cryptography
- CS 361S Network Security and Privacy or
CS 378H Network Security and Privacy: Honors
CUTTING EDGE TOPICS
Students will also need to take any two of the following elective classes:
- CS 349 Contemporary Issues in Computer Science
- CS 378 Ethical Hacking
Maximum of one advanced systems course from this list:
- CS 350C Advanced Architecture
- CS 360V Virtualization
- CS 375 Compilers
- CS 378 Multicore Operating Systems Implementation
- CS 378(H) Concurrency
*In some cases, the graduate course CS395T: Cybersecurity and Law may be substituted for an elective. Please note that undergraduates must be approved to register for graduate classes, and that they may only do so the day before classes start. For more information on that process, please consult your advisor.
If you completed CS 429 during the Fall 2019 semester or before, you may complete this version of the UTCS Security Concentration.
These courses may change and additional courses may be added in the future.



